Request for Callback
Fill out this form to download.

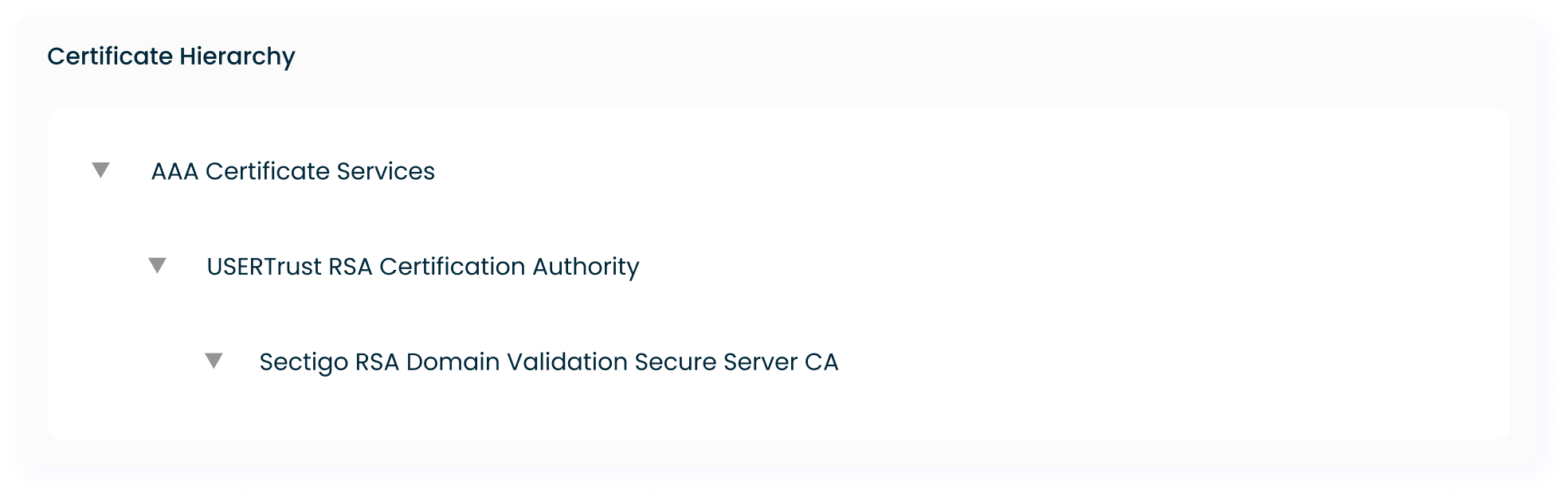
Our data centers are certified to meet rigorous environmental and energy
management standards.
Certifications listed may not be available at all IBX facilities within this
metro. For a complete list, visit our Certifications page.






Expand smERP is secured by 2048bit encryption for all data communication through the internet.

Capture leads effortlessly with ezisales that centralizes all your lead generation efforts.

Users in Expand smERP can be restricted by IP address. Basically user access can be limited to an office network with a given IP address.

Users can be locked to a specific desktop or laptop. Hence the user can only access ERP from that specific desktop or laptop.

Data is on cloud, stored in multiple geo locations ensuring maximum safety. This backup is automatic.

Each customer has the private database and not a shared one as in multi tenant ERP

Users can be restricted to specific modules of the software. The users can be also assigned edit or delete or read only permissions for each module.

Admin user of ERP can request a full database backup of Expand smERP. The system will automatically dump a copy on the configured personal google drive of the administrator.

The data backup is an MS SQL backup file. This file can be restored in any MS SQL server software. MS SQL express edition is freely available on the internet. Once restored the data can then be migrated to any 3rd party database or excel or text files are required. It does not require any secret key or password to restore the data file.

Small, medium and large organizations count on eDominer data security and protection to meet their needs. We take security very seriously and have developed a comprehensive set of practices, technologies and policies to help ensure your data is secure. If you are currently maintaining your data on personal computers or your own servers, the odds are that we offer a better level of security than what you currently have in place. This document outlines some of the mechanisms and processes we have implemented to help ensure that your data is protected. Our security practices are grouped in four different areas: Physical Security; Network Security; People Processes and Redundancy and Business Continuity.

Our datacenters are hosted in some of the most secure facilities available today in locations that are
protected from physical and logical attacks as well as from natural disasters such as earthquakes, fires,
floods, etc.
1. 7x24x365 Security. The data centers that host your data are physically secured and physically restricted
zones.
2. Video Monitoring. Each data center is monitored 7x24x365.
3. Access to Expand ERP data centers is tightly restricted and physically not allowed unless authorized.
Undisclosed multiple locations.
4. Fire Prevention. The Expand ERP host data centers are guarded by industry standard fire prevention and
control systems.

Designing and running data center infrastructure requires not just technology, but a disciplined approach to
processes. This includes policies about escalation, management, knowledge sharing, risk, as well as the day to
day operations. Expand ERP host s security team has years of experience in designing and operating data
centers and continually improves our processes over time. Expand ERP and it s host are performing in
individual capacity to develop world class practices for managing security and data protection risk.
1. Select Employees. Only employees with the highest clearance have access to our data center data.
Employee access passwords are strictly regulated. We limit access to customer data to only a select few of
these employees who need such access to provide support and troubleshooting on our customers behalf.
2. Audits. Audits are regularly performed and the whole process is reviewed by management.
3. As Needed Basis. Accessing data center information as well as customer data is done on an as needed
only basis (i.e. as part of a support incident), or by senior security management to provide support and
maintenance.

One of the fundamental philosophies of cloud computing is the acknowledgment and assumption that
computer resources will at some point fail. We have designed our systems and architecture with that in mind.
1. Power Redundancy. Expand ERP host configures its servers for power redundancy from power supply to
power delivery.
2. Internet Redundancy. Expand ERP host is connected to the world and you through multiple Tier 1 ISPs. So if
any one fails or experiences a delay, you can still reliably get to your applications and information.
3. Redundant Network Devices. Expand ERP host data center runs on redundant network devices (switches,
routers, security gateways) to avoid any single point of failure at any level on the internal network.
4. Geo Mirroring. Customer data is mirrored in a separate geographic location for Disaster Recovery and
Business Continuity purposes.
5. Data Protection & Back up. User data is backed up periodically across multiple servers, helping protect the
data in the event of hardware failure or disaster.

Expand ERP team values the work done by security researchers in improving the security of our service offerings and we are committed to working with the community to verify, reproduce, and respond to legitimate reported vulnerabilities. Please submit security issues at [email protected]
We request that no part of this document be reproduced by any means or transmitted without the written permission of eDominer Technologies. This information is considered privileged and confidential, and its release would offer substantial benefit to competitors offering similar services. This document includes customer details of eDominer, currently using or have used eDominer products and services. Therefore, it is the position of eDominer Technologies that the use or release of the information contained in this document other than an evaluation of its contents as a basis for contract award is prohibited, and materials herein are not considered subject to release.
This document is for information purpose only. eDominer MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS DOCUMENT. eDominer and Peopleware India logo are either registered trademarks or trademarks of eDominer Technologies Private Limited in India. The names of actual companies and products mentioned herein may be the trademarks of their respective owners.
Hosted on Certified Data Centers for Highest Level of Data Protection and Reliability.





